
Howl - Bespoke System Analysis Solution

Howl - Bespoke System Analysis Solution
Introducing Howl, an innovative distributed analysis platform for researchers and security professionals.
Howl facilitates research into operating systems and application behaviour; including process monitoring, binary analysis and system change detection. Howl also provides the ability to run dynamic analyses while collecting live data from multiple network endpoints, allowing you to compare variations across platforms efficiently.
Effortlessly collects and tracks OS events across endpoints, harnessing the power of intuitive visualisations, in-built alerting, and automated analysis.
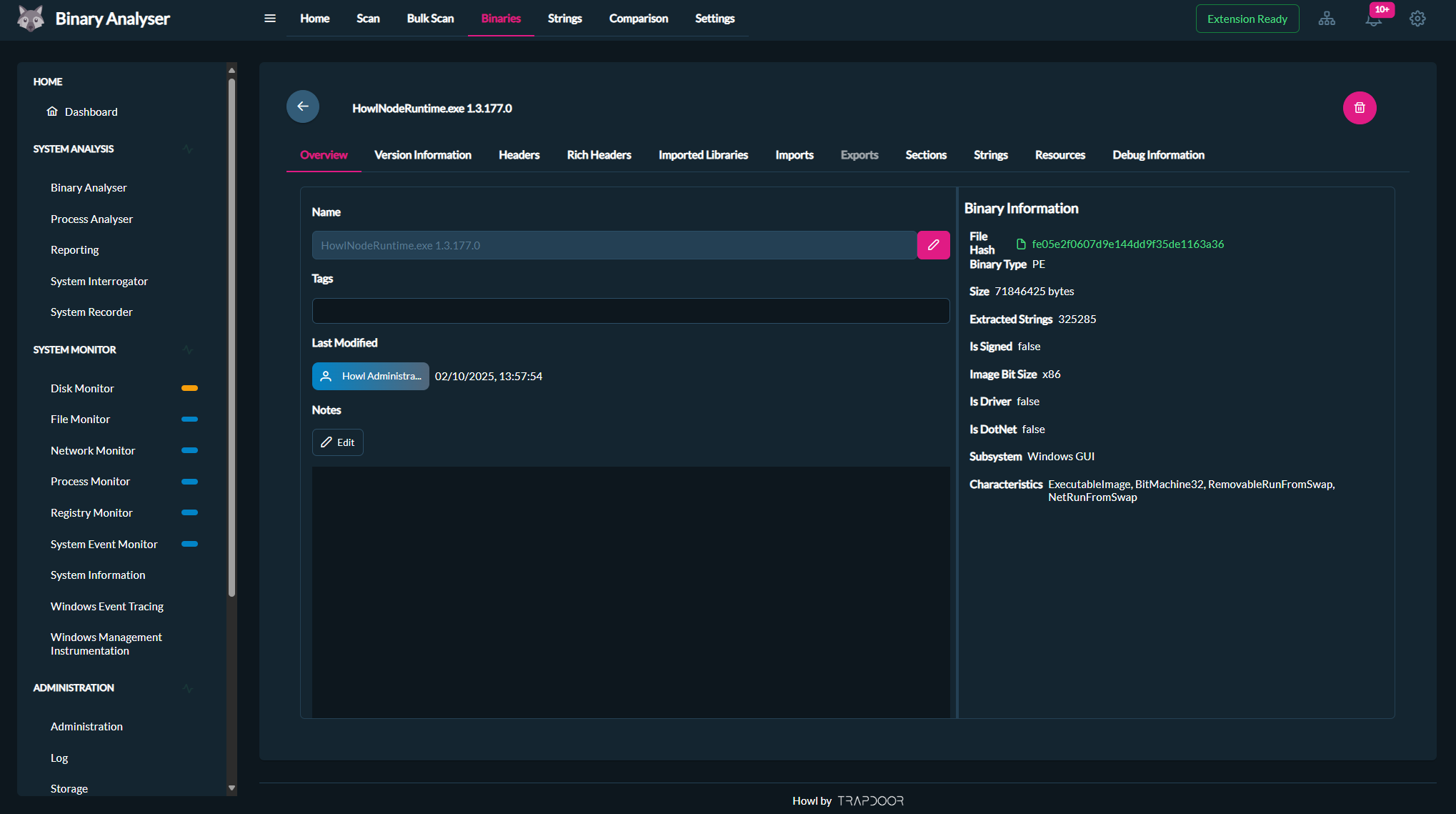
The Binary Analyser is a powerful extension designed for in-depth static analysis of binary files across your Howl Nodes. It provides valuable insights into Portable Executable (PE) files, including headers, sections, imports, exports, strings, debug information, and more. Use the Binary Analyser to uncover vulnerabilities, ensure software reliability, and gain a deeper understanding of your compiled code—all before deployment.
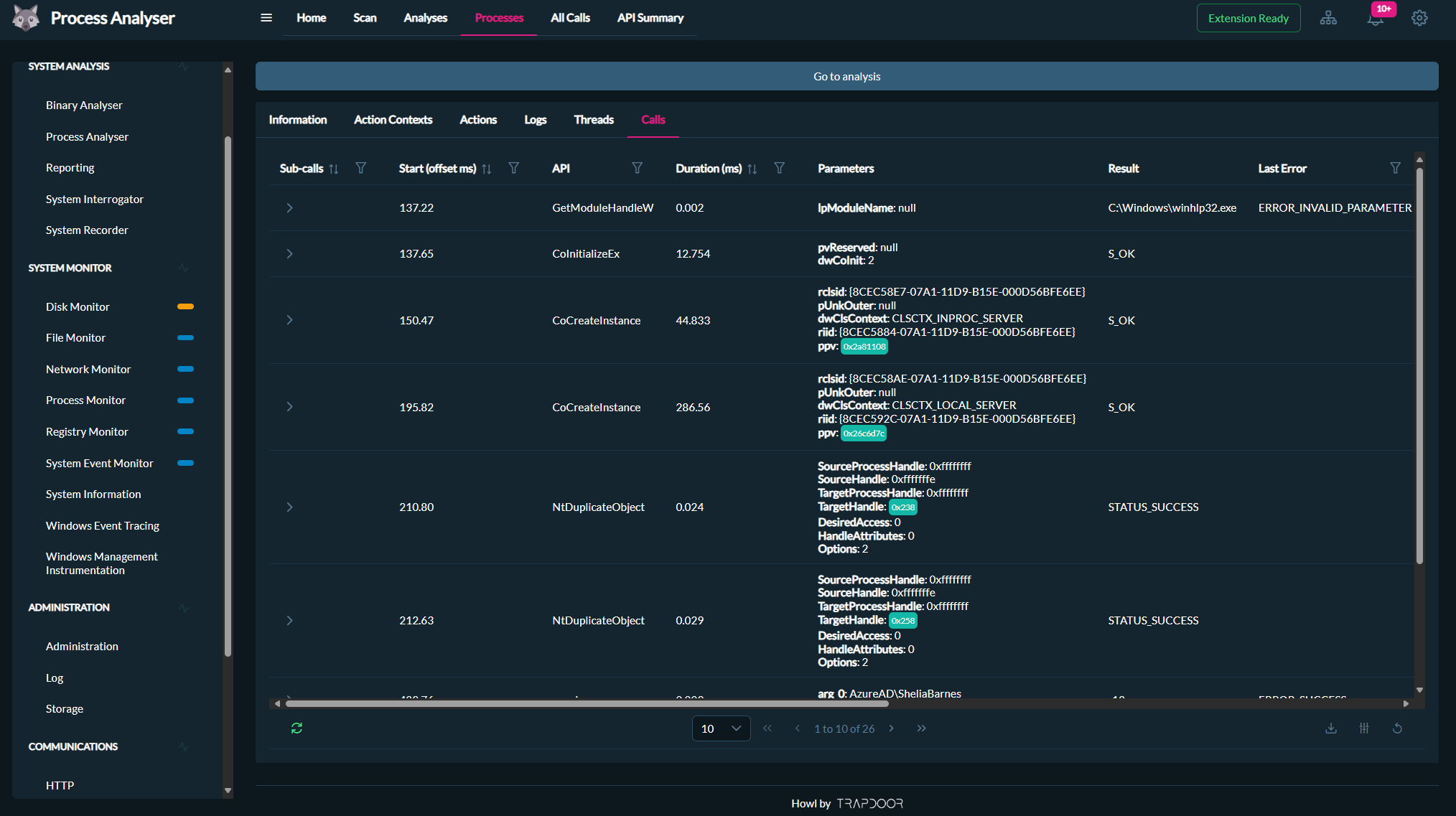
The Process Analyser can be executed across multiple nodes in a Howl network. Each analysis is tailored for a specific target executable, accepting parameters such as arguments, working directory, a hard timeout, and a post-analysis delay.
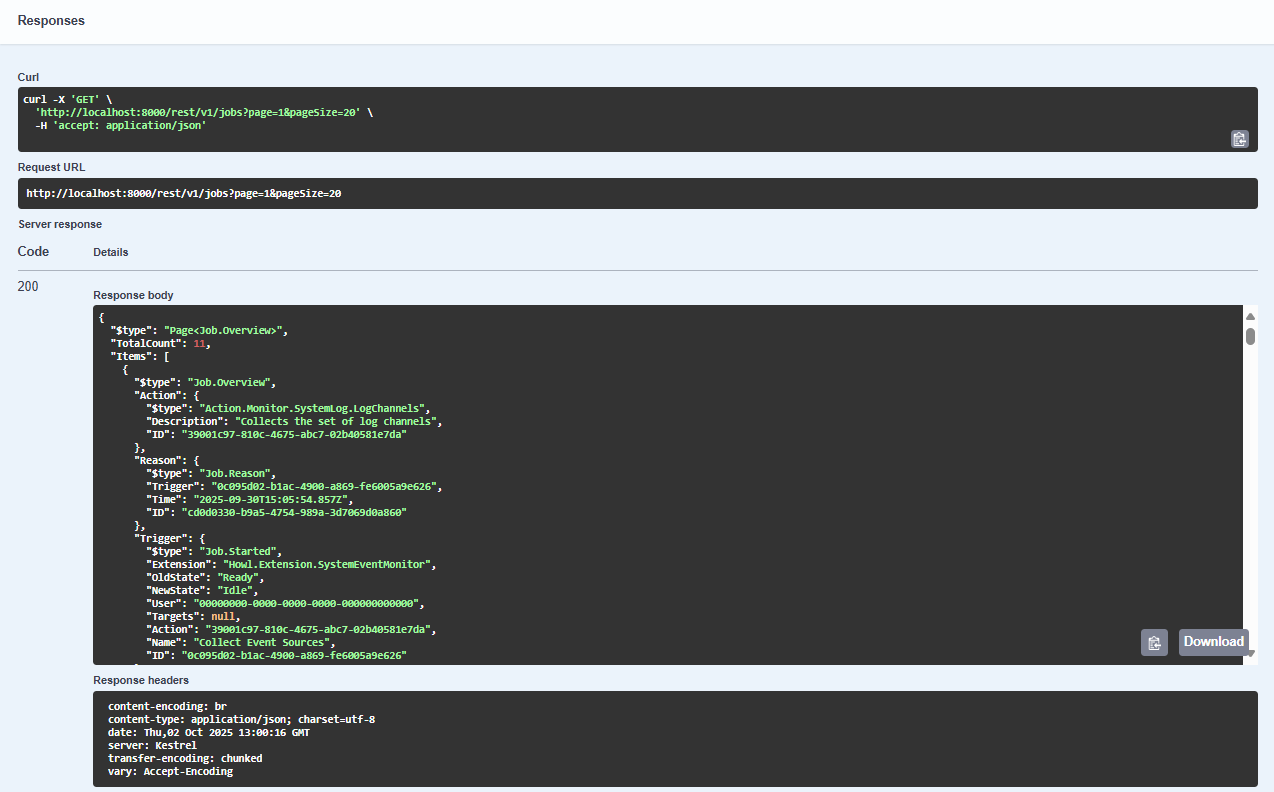
Our REST API offers a comprehensive set of endpoints designed to interact with core system components. It allows developers to query data, manage configurations, trigger actions, and monitor system events programmatically. This enables seamless integration with external platforms, automation tools, and custom applications.
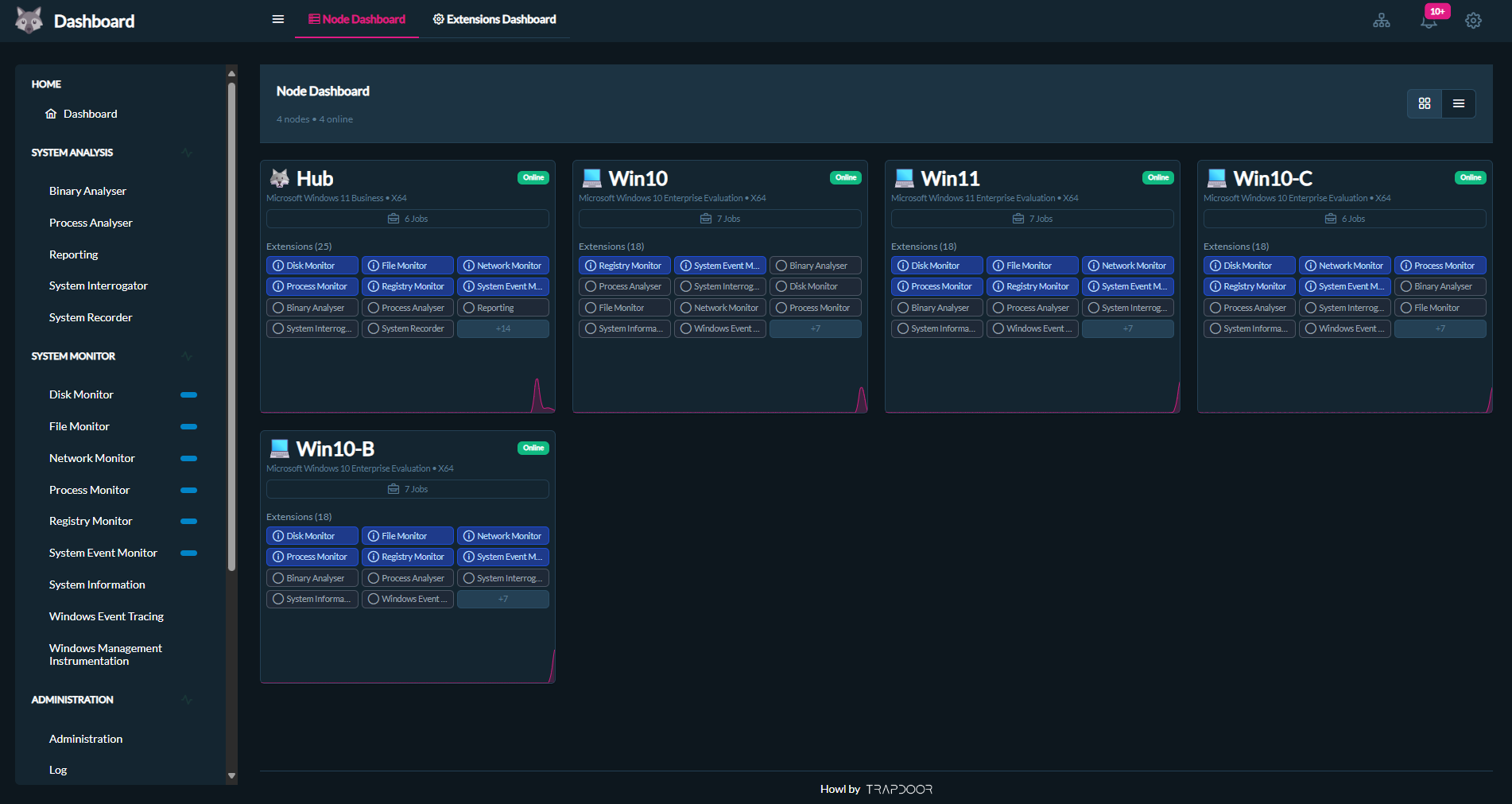
Efficiently manage and deploy jobs across multiple nodes to isolate processes, balance workloads, and enhance system resilience. This functionality allows for distributed execution, helping to reduce bottlenecks and improve fault tolerance in complex environments.
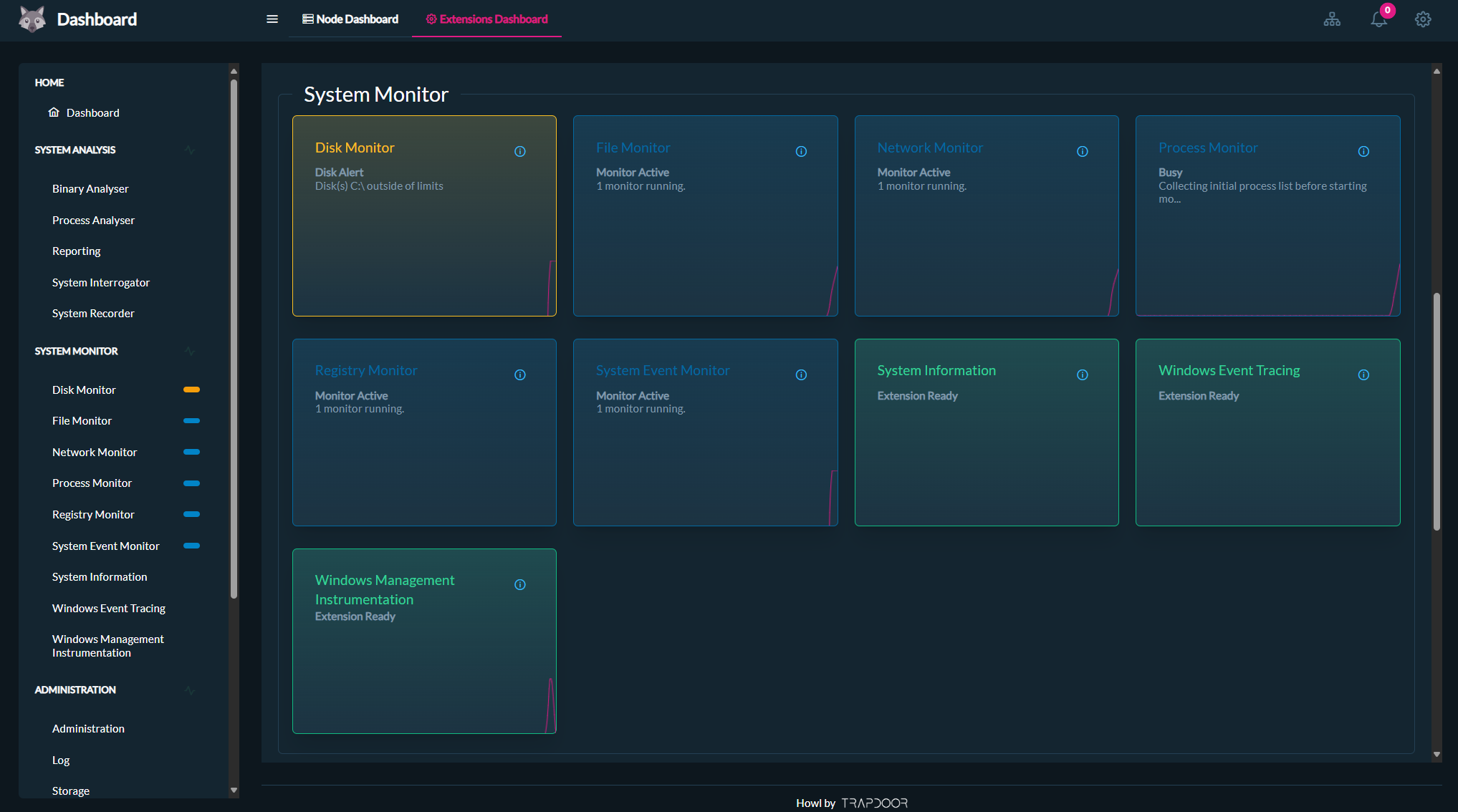
Continuously track and analyse system activity through a robust set of monitoring tools, including disk usage, file system changes, network traffic, and registry modifications. Designed to support cybersecurity research and threat analysis, these monitors provide real-time visibility into system behavior, helping uncover suspicious patterns, investigate incidents, and strengthen overall security posture.
Easily configure and control user access levels to ensure secure and compliant operations.
Generate detailed reports and export insights in various formats for audits, analysis, or sharing.
Visualise key metrics and system activity in a centralised, customisable interface.
Track and respond to system events as they happen for improved situational awareness and security.


